As 2015 comes to a close, it’s time to gain perspective of the future by taking a look back at the present year’s events – in this case, the ransomware.
Some Quick Stats about the Ransomware’s Menace in 2015
• A new variant of the ransomware family – Teslacrypt, was seen in early 2015. It specifically targets computers with saved games files. Read more about Teslacrypt here.
• A massive surge was detected in the CTB Ransomware – a relatively new variant.
• India seemed to have been hit with the highest number of ransomware attacks this year; accounting to 16000 infections.
• The FBI reported a loss of $18 million because of ransomware attacks worldwide.
Ransomware infections are deemed nasty to such a level that even the FBI stated that they often advise people to pay the ransom. Joseph Bonavolonta, Assistant Special Agent in Charge of the Cyber and Counterintelligence Program in the FBI’s Boston office quoted “The ransomware is that good… To be honest, we often advise people just to pay the ransom.”
So, what’s the prediction for ransomware in 2016?
By the looks of the alarming rate at which the ransomware family is growing, it is wise to assume that this malware is here to stay and not going away anytime soon. For 2016, here’s what ransomware authors may be gearing up for:
1. Getting more personal – hackers may threaten people of releasing encrypted information in public. Instances of this have already occurred. ‘Chimera’ – a recently launched ransomware campaign in Germany, threatened to release the victims’ encrypted files in public, if the ransom was not paid.
2. Targeting Macs – with Mac becoming more popular among users, they are likely to become an attractive prey for ransomware.
3. Extending the ransomware circle – rookie cybercriminals may start offering ransomware as a service, transforming it into a large-scale business-like operation.
4. Targeting Android – attempts of bringing ransomware to the mobile platform have already been noticed in 2015; a popular example is SimpleLocker. In the coming year, we can expect advanced and more complex variants of the same and others alike.
5. Better delivery – hackers will use more sophisticated mechanisms to spread ransomware and more valuable ways to extort money from their victims.
6. Other targets – as more users are becoming aware and getting educated about how to fight ransomware, hackers will target avenues which are still security-deficient such as smart TVs, smart houses, smart fridges, Internet-enabled cars; in short, the Internet of Things.
7. Life Threatening – Frighteningly, ransomware attacks can turn out to be more than a digital threat to people – it can become life-threatening. Attackers are now suspected to go after lifesaving medical devices. There could be a horrid situation where a patient is demanded to pay a ransom in order for their pacemaker to be released from a ransomware’s clutches. Read more on this here.
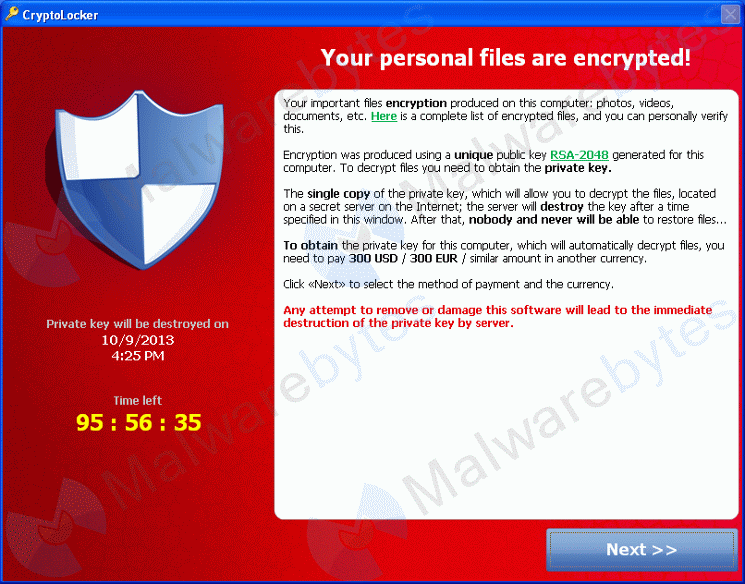
Steps you Must Take
Cyber criminals don’t take time off from creating and improving upon their tactics and that’s why it is essential that we don’t let our guard down against them. Here are some of the best ways you can protect your device from ransomware:
• Never download attachments or click links in emails received from unwanted or unexpected sources, even if the source looks familiar.
• Don’t respond to unwanted pop-up ads or alerts while visiting unfamiliar or even familiar websites.
• Apply all recommended security updates to your OS, software, and Internet browsers, if not already.
• Take regular backups of all the important files you have on your computer. We recommend you to begin the backup procedure offline and not when you are connected to the Internet. Doing this will ensure that you do not have to meet the ransomware’s demands.
• Have a security software installed in your PC that efficiently blocks spam and malicious emails, and automatically restricts access to malicious websites. Antivirus has an inbuilt anti-ransomware defense that detects and stops ransomware that encrypt data. This defense mechanism works on a behavior-based module – which means, it analyzes programs based on their behavior and the activities carried by them on the users machine. This helps Quick Heal detect malware like ransomware in real-time and prevent possible infections. This anti-ransomware feature remains active in the system even if the antivirus software itself is turned off for some reason.
Courtesy :- Quick Heal