Web Infrastructure
Web Infrastructure refers to the hardware, software, and network resources required to support and operate a website or web application. It includes all the elements that make a website functional, accessible, and scalable.
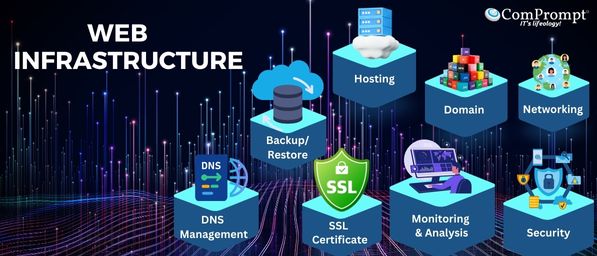
Key Components of Web Infrastructure
Hosting Servers
A server is a computer or software that provides services, data, or resources to other computers (clients) over a network. Hosting servers can come in various types, such as shared, dedicated, VPS, and cloud servers, each offering different levels of control, performance, and scalability.
Types of Servers :
Domain
A domain is the unique address used to access a website on the internet, like “example.com.” It serves as an easy-to-remember name that directs users to a specific IP address where a website’s files are stored.
Domains are made up of a name (e.g., “example”) and an extension (e.g., “.com”), with many extensions available, such as “.net,” “.org,” or country-specific ones like “.uk.” Registering a domain is the first step in establishing an online presence, as it becomes the website’s recognizable identity.
SSL Certificates
SSL (Secure Sockets Layer) certificates are digital certificates that verify the identity of a website and establish a secure connection between a user’s web browser and the website’s server. This secure connection ensures that data transmitted between the two parties is encrypted, protecting it from eavesdropping and tampering. SSL certificates enable websites to use HTTPS, which is more secure than HTTP.
DNS Management
DNS (Domain Name System) management involves configuring and maintaining DNS records that link domain names to their corresponding IP addresses. DNS management allows website owners to control how users access their site by setting up records like A (address), CNAME (canonical name), MX (mail exchange), and TXT (text) records.
Proper DNS management ensures that domain names point to the correct servers for web hosting, email, and other services, optimizing website accessibility and performance.
Backup/Restore
Backup and Restore are essential processes in data management to ensure the safety and availability of information.
- Backup involves creating copies of data to protect it against loss, corruption, or damage. These backups are stored in secure locations, often separate from the primary data source, such as on external drives or cloud storage. Regular backups are critical to minimize potential data loss.
- Restore is the process of retrieving and recovering backed-up data to its original or another location. In case of data loss, corruption, or system failure, restore operations allow users to recover their data from the backup, ensuring continuity and minimizing downtime.
Security
Web Security refers to the measures and technologies used to protect websites, web applications, and web users from cyber threats and attacks. It encompasses a variety of practices aimed at safeguarding sensitive data, maintaining user privacy, and ensuring the integrity and availability of online services.
- Authentication and Access Control: Ensuring that only authorized users can access certain parts of a website.
- Data Encryption: Protecting data in transit with SSL/TLS encryption to prevent interception.
- Firewalls and Intrusion Prevention: Blocking unauthorized access and detecting suspicious activity.
Monitoring & Analysis
Monitoring and analysis involve tracking and examining the performance, security, and behavior of a website or application to ensure it operates smoothly and efficiently.
Monitoring tools collect real-time data on metrics like uptime, page load speed, server response times, and error rates. Analysis then helps interpret this data to identify patterns, detect issues, and make informed improvements.
Networking
Networking refers to the process of connecting computers and devices to share resources and data. It’s the backbone of communication between systems and enables the internet, intranets, and other essential business technologies.
Key components include routers, switches, firewalls, and network cables, along with network configurations like IP addressing and subnetting.